Lot 118, Lane 1, 1st Avenue, Gwarimpa Estate, Abuja - Nigeria
Now Hiring: Are you a driven and motivated 1st Line IT Support Engineer?

Lot 118, Lane 1, 1st Avenue, Gwarimpa Estate, Abuja - Nigeria
Now Hiring: Are you a driven and motivated 1st Line IT Support Engineer?

NextBewe
Infrastructure Setup/Management
20 June, 2023
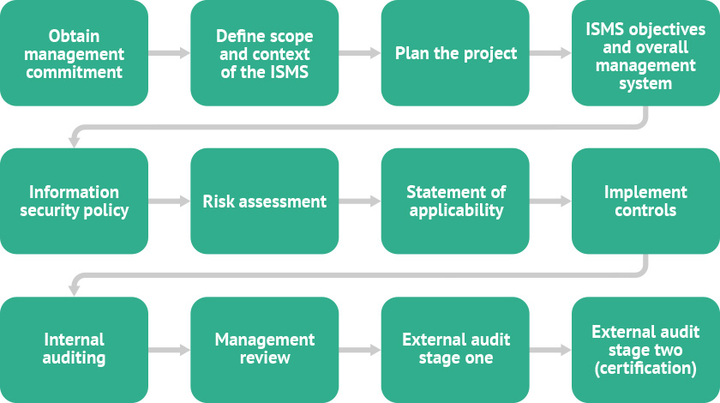
In today's interconnected and fast-paced world, businesses of all sizes must prioritize the establishment of a robust network infrastructure. The efficiency and reliability of your network play a crucial role in the success of your operations. In this comprehensive guide, we will explore the key components and best practices for setting up a powerful networking infrastructure that meets ISO 27001 certification standards, this is how I designed and implemented a network for 50 users while working as an IT Manager.
Understanding the Importance of Networking Infrastructure Setup
A strong networking infrastructure serves as the backbone of any organization's IT ecosystem. It enables seamless communication, facilitates data transfer, and supports essential business applications. Without a well-designed and properly implemented network, your employees may face slow connection speeds, frequent downtime, and compromised data security.
Building a Solid Foundation: Network Design and Architecture
The first step in setting up an effective networking infrastructure is designing a solid foundation. This involves mapping out the network topology, determining the number of devices, and planning for future scalability. A well-designed network architecture ensures optimal performance, minimizes bottlenecks, and enables easy troubleshooting. Factors such as network segmentation, redundancy, and load balancing should be considered to ensure high availability and fault tolerance.
Here are a few steps and tools I looked into before settling for what works best for my organization;
Step 1: Assess Requirements and Objectives
- Understand the specific requirements and objectives of your organization's network.
- Determine factors such as the number of devices, expected traffic volume, and future scalability needs.
Step 2: Map Network Topology
- Create a visual representation of your network infrastructure, including devices, connections, and their relationships.
- Use network diagramming tools such as Cisco Network Assistant, Microsoft Visio, or draw.io to map out the network topology.
Step 3: Determine Network Segmentation
- Identify logical divisions or segments within your network for better management and security.
- Determine the level of segmentation required based on factors like departmental needs, data sensitivity, and regulatory compliance.
Step 4: Consider Redundancy and High Availability
- Plan for redundancy to minimize single points of failure and ensure high availability.
- Determine where redundancy is required, such as network links, switches, or firewalls, and design backup mechanisms accordingly.
Step 5: Address Load Balancing
- Distribute network traffic evenly across multiple devices or paths to optimize performance and prevent bottlenecks.
- Consider load balancing techniques, such as round-robin, least connections, or weighted distribution, based on your network requirements.
Step 6: Select Routing Protocols
- Choose the appropriate routing protocols to facilitate efficient data transfer between network devices.
- Common routing protocols include OSPF (Open Shortest Path First), BGP (Border Gateway Protocol), and EIGRP (Enhanced Interior Gateway Routing Protocol).
Step 7: Use Network Simulation Tools
- Utilize network simulation tools to model and test different network scenarios before implementing changes.
- Tools like Cisco Packet Tracer, GNS3, or EVE-NG allow you to simulate network behavior and assess the impact of design decisions.
Step 8: Ensure Security Measures
- Incorporate security measures into your network design, such as firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs).
- Consider the placement of security devices and define access control policies to protect your network from unauthorized access.
Step 9: Document and Document
- Document your network design, including network diagrams, IP address schemes, device configurations, and security policies.
- Use documentation tools like Confluence, Microsoft SharePoint, or Wiki platforms to maintain a centralized repository of network-related information.
Step 10: Periodic Review and Optimization
- Regularly review and assess your network design to identify areas for improvement.
- Use network monitoring tools like SolarWinds, PRTG Network Monitor, or Zabbix to gather performance data and analyze network behavior.
Selecting the Right Network Equipment
Start by selecting appropriate routers, switches, and firewalls based on your organization's specific requirements. Consider factors such as port density, throughput, security features, and compatibility with your existing hardware and software. Additionally, investing in enterprise-grade equipment from reputable vendors ensures long-term reliability and support.
Implementing Network Security Measures
Securing your networking infrastructure is paramount to protect sensitive data and maintain the integrity of your business operations. Implementing robust security measures helps prevent unauthorized access, data breaches, and network vulnerabilities. Some essential security practices include setting up firewalls, implementing virtual private networks (VPNs) for remote access, regularly updating firmware and software, and conducting periodic security audits.
This is the whole essence of getting ISO 27001 certified, so this must always be at the back of your mind through the planning and implementation of your network.
Optimizing Network Performance
To ensure optimal network performance, it is crucial to regularly fine-tune and optimize your infrastructure. One key aspect is effectively managing network bandwidth. By prioritizing critical applications and limiting bandwidth for non-essential activities, you can prevent congestion and ensure a smooth user experience. Additionally, regularly monitoring network performance, analyzing traffic patterns, and proactively addressing bottlenecks will help maintain an efficient and reliable network. The best advice for this phase would be to get a firewall device with SD-WAN capabilities, with this you can use to uplinks and do a lot of traffic shaping according to your needs, It’s also a good mechanism to scale through the “Redundancy” requirements of ISO 27001. I used FortiGate for this purpose, configured HA and SD-WAN and my network had 99.99% uptime, same as my firewall.
Implementing Network Monitoring and Management Tools
Investing in network monitoring and management tools is essential for effectively managing and maintaining your networking infrastructure. These tools provide real-time visibility into your network, enabling you to monitor performance metrics, detect anomalies, and troubleshoot issues promptly. By leveraging automation and centralized management, you can streamline network operations, reduce downtime, and improve overall efficiency. Also, my conscience wouldn’t allow me have the organization spending too much on tools, even though it’s in their best interest, so from the onset, I started researching open source tools to compliment wherever I could swap out paid tools to keep costs down. So for network monitoring, you can use tools like Snort, Zabbix, etc. There’s always a learning curve, however, I assure with the amount of sleepless nights you’ll encounter, there’ll be enough time to learn, as this challenge is very exciting. Depends on your perspective though.
Planning for Scalability and Future Growth
As your business grows, your networking infrastructure must be able to scale seamlessly to accommodate increased traffic, devices, and users. Planning for scalability from the beginning will save you and the organization time and resources in the long run. Consider future-proofing your network by using modular equipment, implementing scalable architectures, and regularly evaluating your capacity requirements. This proactive approach ensures that your network can adapt and grow alongside your business needs. We are essentially talking about servers, routers, firewalls and switches here, this is where you must not cut cost, unless you’re certain the organization has reached it’s limits for scalability. The firewall devices are most like going to be your point of concern, ensure to go through datasheets as much as you can to have a good understanding of your requirements. Another good measure of scalability is using the premise to measure or asking the top management key questions about the business and it’s plan to stay at the same location for a long period of time.
Conclusion
The key areas you can focus on even without ISO, are;
IAM, SIEM, Endpoint security, Vulnerability management, Network Security, Data loss prevention, Network access control, Patch management, Backup and recovery, and cryptography. In my opinion every network should have all these criteria fulfilled, this way you can be audited anytime and be compliant.
Setting up a network infrastructure that meets ISO 27001 certification standards is a critical investment for any organization. By following the best practices outlined in this guide, you can create a robust and reliable network that supports your business operations and fosters growth. Remember to prioritize network design, select the right equipment, implement strong security measures, optimize performance, and plan for scalability. With a well-designed and properly implemented networking infrastructure, you can lay the foundation for success in today's interconnected world while meeting ISO 27001 certification standards. Even artificial intelligence will have a hard time compromising your network.
Key Takeaways
Design a Solid Foundation
Implement Robust Security Measures
Optimizing Performance and Scalability