Lot 118, Lane 1, 1st Avenue, Gwarimpa Estate, Abuja - Nigeria
Now Hiring: Are you a driven and motivated 1st Line IT Support Engineer?

Lot 118, Lane 1, 1st Avenue, Gwarimpa Estate, Abuja - Nigeria
Now Hiring: Are you a driven and motivated 1st Line IT Support Engineer?

FeySem Enterprise
Cyber Security
10 October, 2023
Outline:
1. Introduction
2. Understanding Penetration Testing
- Definition and Purpose
- Types of Penetration Testing
3. The Importance of Blackbox Penetration Testing
4. The Process of a Blackbox Penetration Testing Exercise
- Pre-engagement Phase
- Reconnaissance and Information Gathering
- Vulnerability Assessment and Exploitation
- Reporting and Recommendations
5. Advantages of Blackbox Penetration Testing
- Realistic Simulation of External Threats
- Identification of Unknown Vulnerabilities
- Assessment of Overall Security Posture
6. Skillry's Approach to Blackbox Penetration Testing
- Expert Team and Methodologies
- Comprehensive Testing Techniques
- Clear and Actionable Reporting
7. Conclusion
8. FAQs (Frequently Asked Questions)
1. What is the difference between blackbox and whitebox penetration testing?
2. How often should a blackbox penetration testing exercise be conducted?
3. Is blackbox penetration testing legal?
4. Can blackbox penetration testing disrupt normal business operations?
5. How long does a blackbox penetration testing exercise typically take?
A Blackbox Penetration Testing Exercise for a Client by Skillry
Introduction
In today's digital landscape, organizations face an ever-increasing number of cyber threats. To safeguard their sensitive data and critical systems, businesses employ various security measures, one of which is penetration testing. This article focuses on a specific type of penetration testing known as blackbox testing and explores how Skillry conducts a blackbox penetration testing exercise for its clients.
Understanding Penetration Testing
Definition and Purpose
Penetration testing, often referred to as ethical hacking, is a proactive security assessment that aims to identify vulnerabilities and weaknesses within an organization's systems, networks, or applications. The primary purpose of penetration testing is to simulate real-world attacks and evaluate the effectiveness of existing security controls.
Types of Penetration Testing
Penetration testing can be categorized into different types based on the level of knowledge provided to the testing team. These include blackbox testing, whitebox testing, and greybox testing. In this article, we focus on blackbox penetration testing, which simulates an external attacker with no prior knowledge of the target environment.
The Importance of Blackbox Penetration Testing
Blackbox penetration testing is an essential component of a comprehensive security strategy. By mimicking the actions of real attackers, it provides a realistic assessment of an organization's security posture from an external perspective. This type of testing helps identify vulnerabilities that may go unnoticed through other security measures, such as internal testing or vulnerability scanning.
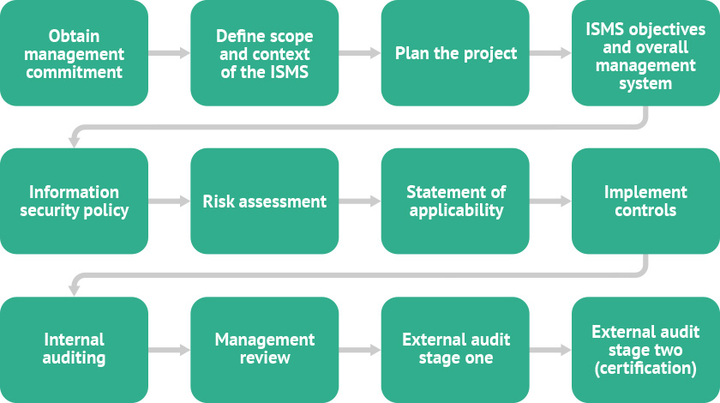
The Process of a Blackbox Penetration Testing Exercise
Like all penetration testing exercises, a blackbox penetration testing exercise typically involves the following phases:
Pre-engagement Phase
During this phase, the testing team and the client establish the scope, objectives, and rules of engagement for the exercise. They define the target systems, networks, or applications to be tested, along with any specific constraints or limitations.
Reconnaissance and Information Gathering
In this phase, the testing team gathers information about the target environment using publicly available sources, such as search engines, social media, and domain registries. This information helps in identifying potential entry points and understanding the organization's online presence.
Vulnerability Assessment and Exploitation
Using the information gathered, the testing team performs a thorough vulnerability assessment of the target systems. They use various techniques and tools to identify weaknesses and attempt to exploit them, simulating real-world attack scenarios. The goal is to gain unauthorized access, escalate privileges, and extract sensitive information.
Reporting and Recommendations
After completing the testing phase, the team prepares a detailed report highlighting the vulnerabilities discovered, the impact they could have on the organization, and recommendations for remediation. The report includes actionable steps to enhance security, prioritize remediation efforts, and mitigate identified risks.
Advantages of Blackbox Penetration Testing
Blackbox penetration testing offers several advantages for organizations:
Realistic Simulation of External Threats
By assuming the role of external attackers, blackbox testing provides a realistic assessment of an organization's vulnerabilities. It helps organizations understand their security posture from an outsider's perspective, allowing them to take proactive measures to strengthen their defenses.
Identification of Unknown Vulnerabilities
Blackbox testing uncovers vulnerabilities that may be unknown to the organization. Since the testing team has no prior knowledge of the target environment, they can identify blind spots and weaknesses that internal security measures may have missed.
Assessment of Overall Security Posture
Blackbox penetration testing provides a holistic evaluation of an organization's security controls. It assesses the effectiveness of not only technical defenses but also human factors, such as user awareness, incident response procedures, and security policies.
Skillry's Approach to Blackbox Penetration Testing
Skillry adopts a systematic and comprehensive approach to blackbox penetration testing:
Expert Team and Methodologies
Skillry's testing team consists of experienced professionals who possess a deep understanding of the latest attack techniques and methodologies. They follow industry best practices, frameworks, and compliance standards to ensure thorough and effective testing.
Comprehensive Testing Techniques
Skillry employs a wide range of testing techniques to uncover vulnerabilities. These include network scanning, web application testing, social engineering, wireless network assessment, and more. This multi-faceted approach ensures a comprehensive evaluation of an organization's security posture.
Clear and Actionable Reporting
Skillry's penetration testing reports are comprehensive yet easy to understand. They provide clear descriptions of vulnerabilities, their potential impact, and practical recommendations for remediation. Skillry believes in delivering actionable insights that help organizations strengthen their security defenses.
Conclusion
A blackbox penetration testing exercise conducted by Skillry provides organizations with valuable insights into their security vulnerabilities and helps them proactively strengthen their defenses. By simulating real-world attacks, organizations can identify weaknesses, enhance their security posture, and mitigate the risk of potential breaches.
FAQs (Frequently Asked Questions)
1. What is the difference between blackbox and whitebox penetration testing?
- Blackbox penetration testing simulates an external attacker with no prior knowledge of the target environment, while whitebox penetration testing involves testing with full knowledge of the internal systems and infrastructure.
2. How often should a blackbox penetration testing exercise be conducted?
- The frequency of blackbox penetration testing depends on various factors, including the organization's industry, regulatory requirements, and the evolving threat landscape. Generally, it is recommended to conduct such exercises at least annually or after significant changes to the infrastructure.
3. Is blackbox penetration testing legal?
- Yes, blackbox penetration testing is legal when conducted with proper authorization from the organization being tested. It is crucial to engage ethical and certified professionals for conducting these exercises.
4. Can blackbox penetration testing disrupt normal business operations?
- Blackbox penetration testing is carefully planned and executed to minimize disruptions to normal business operations. The testing team takes precautions to ensure that any impact on operations is minimal and controlled.
5. How long does a blackbox penetration testing exercise typically take?
- The duration of a blackbox penetration testing exercise varies depending on the size and complexity of the target environment. It can range from a few days to several weeks. Skillry tailors the testing timeline to the specific needs and requirements of each client to ensure thorough testing without causing unnecessary disruptions.